The Critical Role of Access Control in Modern Computing
On March 6, 2023, cybersecurity giant Crowdstrike experienced a two-hour outage due to an authorization error. This incident serves as a stark reminder of the vulnerabilities inherent in our increasingly complex digital infrastructure. As we embrace cloud computing, distributed systems, and zero-trust architectures, the importance of robust access control becomes paramount. The Crowdstrike outage highlights how even minor errors in authorization can have far-reaching consequences in our interconnected digital landscape, underscoring the critical need for vigilance and precision in cybersecurity practices.
Understanding the Crowdstrike incident requires distinguishing between authentication and authorization. Authentication verifies identity, while authorization determines access rights. In this case, the system correctly identified users but failed to grant proper permissions. This distinction is fundamental to modern access control systems and will be central to our analysis.
Computer security has advanced significantly since the 1960s and 1970s. Initially, it relied on simple physical access controls and basic passwords, which were adequate for the isolated, large computers of that era. As computing power and connectivity increased, security methods evolved to combat emerging threats, becoming more complex and comprehensive.
Today's digital landscape has transformed cybersecurity. We've moved from protecting individual systems to securing complex, interconnected networks. This change is due to:
- Cloud and distributed computing have rendered perimeter-based security ineffective by dissolving traditional network boundaries.
- Smartphones and connected devices have greatly amplified cybersecurity threats.
- Proliferation of user-friendly hacking tools and government-backed cyberattacks has significantly increased security breach risks.
Modern security architectures use a "defense in depth" approach, incorporating multiple protective layers:
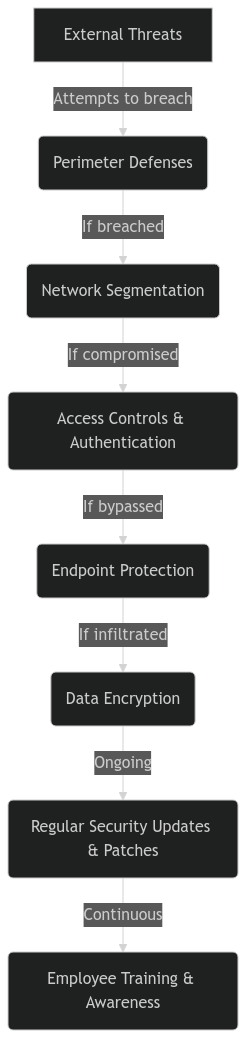
This multi-layered strategy helps safeguard against various threats and minimizes the impact of potential breaches:
- Perimeter defenses (firewalls, intrusion detection)
- Network segmentation
- Access controls and authentication
- Endpoint protection
- Data encryption
- Regular security updates and patches
- Employee training and awareness
This multi-layered approach enhances overall security by creating redundant safeguards against diverse threats:
- Advanced encryption algorithms that secure data both at rest and in transit
- Real-time anomaly detection and response using AI and machine learning
- Advanced identity and access management systems incorporating:
- • Continuous authorization
- • Behavioral analysis
- • Multi-factor authentication
- Zero-trust security verifies all access attempts, treating every user and device as potentially untrustworthy.
Cybersecurity now extends beyond technical solutions, incorporating human factors, organizational processes, and advanced technologies. This holistic approach reflects the complex, interconnected nature of our digital world, where security is no longer solely an IT concern. The CISO has transitioned from a technical specialist to a strategic leader, aligning security with business goals.
Security now influences boardroom decisions, shaping strategy and risk assessment. While employees remain vulnerable to sophisticated social engineering, a well-trained workforce is crucial in defending against complex threats.
Cybersecurity today requires a comprehensive approach. Organizations must integrate security into all aspects of their operations, moving beyond simple firewalls to address the complex, interconnected nature of modern digital systems. Modern security demands an organization-wide culture shift. DevSecOps integrates security throughout the development process from the start. Implementing this approach is challenging, requiring process changes, mindset shifts, and substantial investments in time and resources.
"Adaptive risk management frameworks" seem appealing, but their practical implementation requires careful scrutiny. How truly agile can these frameworks be in the face of rapidly evolving threats? Are organizations prepared to make split-second decisions and pivot their entire security strategy at a moment's notice? We must confront these issues directly.
The complexity of modern security requires professionals to be versatile experts in multiple fields, including technology, psychology, and organizational behavior.
While this comprehensive approach is essential, we should question whether our expectations for security teams are realistic. The Crowdstrike incident demonstrates that even top cybersecurity firms can experience security breaches. This event highlights that in cybersecurity, past success does not ensure future protection.
This event should prompt us to question our assumptions about security providers and the infallibility of established systems.
Cybersecurity demands ongoing innovation and collaboration, but we must approach these challenges critically. We need to fundamentally rethink security in our complex digital world, not just adopt new technologies. Moving forward requires balancing ambition with pragmatism, innovation with analysis, and confidence with skepticism.


At 9:45 AM ET, Crowdstrike's incident response team received numerous alerts from clients unable to access the Falcon platform, their primary cybersecurity defense tool. Engineers quickly identified the issue: a critical malfunction in the identity provider service, blocking user access. After two hours of intensive troubleshooting, full functionality was restored at 11:45 AM, resolving the crisis for Crowdstrike and its clients.
CrowdStrike addressed the incident openly. They quickly published a detailed incident report, explaining that the issue stemmed from an authentication service upgrade gone awry. This transparency rebuilt trust and revealed insights into modern authorization management challenges.
The Crowdstrike incident highlights the rapidly evolving digital landscape. It serves as a warning, revealing the increasing complexities of our interconnected world. Key trends include: 1. Edge computing's growth 2. IoT device proliferation 3. 5G network adoption These developments create a new paradigm where vast amounts of data flow through complex networks, introducing numerous potential vulnerabilities.
Distributed architecture provides exceptional flexibility and growth potential for businesses. However, its interconnected nature also greatly expands vulnerability to cyber threats. Traditional security methods are no longer sufficient in this environment. The new challenge is protecting a dynamic digital ecosystem with unclear boundaries between internal and external networks.
In today's dispersed digital environment, the outdated concept of a secure network perimeter is inadequate. With data and services constantly moving across devices, networks, and cloud platforms, every interaction point becomes a potential vulnerability. Consequently, robust authorization systems are now essential for maintaining security.
Consider, for instance, a modern IoT ecosystem. Smart homes contain numerous connected devices, including thermostats, cameras, appliances, and lighting. These devices communicate with central hubs, cloud services, and each other. Inadequate authorization controls can turn even a minor device, like a smart light bulb, into a potential entry point for attackers to breach the entire home network.
This complexity extends to enterprise environments as well. In today's organizations, employees often use personal devices, work remotely, and collaborate with external partners. This flexibility requires careful management of access rights to balance data security with workplace efficiency.
Advanced authorization mechanisms such as Role-Based Access Control (RBAC), Attribute-Based Access Control (ABAC), and Just-In-Time (JIT) access have become essential in modern security. These systems make sophisticated access decisions based on multiple factors, surpassing traditional binary "allow" or "deny" approaches.
- RBAC (Role-Based Access Control) assigns permissions according to a user's organizational role. For example, a marketing manager and a software developer would have distinct access rights, tailored to their specific job functions and requirements. ABAC takes this a step further, considering not just roles but also other attributes like time of day, location, or device type when making authorization decisions.
- JIT (Just-In-Time) access implements the principle of least privilege by granting temporary, need-based access rights. This approach reduces both the attack window and the potential impact of compromised credentials.
The implementation of these cutting-edge authorization frameworks is akin to conducting a grand symphony in real-time. Each system must orchestrate a complex interplay of decisions, harmonizing vast amounts of contextual data without missing a beat. They're tasked with the Herculean feat of scaling to accommodate millions of users and devices, all while maintaining the tempo of seamless user experience.
But the true crescendo of complexity lies in the organizational realm. Crafting and sustaining access policies demands a virtuoso's understanding of both the technical score and the business composition it accompanies. It necessitates a continuous dialogue between IT maestros, security conductors, and business soloists to ensure that access controls resonate with both security best practices and operational rhythms.
Yet, despite this labyrinth of challenges, the criticality of robust authorization systems cannot be overstated. The Crowdstrike incident serves as a cautionary overture, demonstrating how even a momentary dissonance in authorization can cascade into a cacophony of consequences. For many organizations, the ability to swiftly and precisely modulate access to resources isn't merely a security measure—it's the very pulse of operational continuity.
As we pivot to explore the future of authorization, we find ourselves on the cusp of a new movement in this ever-evolving symphony. The next measures promise to introduce even more sophisticated motifs, weaving artificial intelligence and machine learning into the fabric of access control. This harmonic progression beckons us to consider: how will these emerging technologies reshape the landscape of authorization, and what new challenges and opportunities will they bring to the forefront of cybersecurity?
So, what does best practice look like in this new era of authorization? It's no longer sufficient to view authorization as a static, binary decision-making process. Instead, we must embrace a dynamic, context-aware approach that evolves in real-time.
First, we need to shift our paradigm from perimeter-based security to data-centric protection. In a world of microservices, serverless architectures, and edge computing, the concept of a network perimeter is increasingly obsolete. Authorization must be granular, extending to individual data elements and API calls.
Consider implementing a zero-trust architecture coupled with Just-In-Time (JIT) access. This approach assumes no entity is trustworthy by default and provides access rights only when needed and only for the duration required. For instance, a DevOps engineer might receive elevated permissions to a production environment only for the duration of a specific deployment task.
Leverage the power of graph databases for more sophisticated role-based access control (RBAC). By modeling relationships between users, roles, and resources as a graph, we can implement complex access policies that traditional relational databases struggle to represent efficiently. This approach allows for more nuanced and flexible authorization rules, crucial in today's dynamic organizational structures.
Incorporate behavioral analytics and machine learning into your authorization framework. By establishing baseline patterns of user behavior, anomaly detection algorithms can flag potential security breaches in real-time. For example, if a user suddenly accesses sensitive data from an unusual location or at an atypical time, the system could automatically escalate authentication requirements or revoke access.
As we look to the future, the integration of quantum-resistant cryptography into authorization protocols will become crucial. With the looming threat of quantum computers potentially breaking current encryption methods, organizations must start preparing now. Implementing post-quantum cryptographic algorithms for secure key exchange and digital signatures in authorization processes will be vital for long-term security.
Furthermore, the rise of Self-Sovereign Identity (SSI) and decentralized identifiers (DIDs) will revolutionize how we approach authorization. These technologies promise to give individuals greater control over their digital identities while providing more robust and privacy-preserving methods of authentication and authorization.
Consider the potential of intent-based authorization systems powered by advanced natural language processing. These systems could interpret user queries and actions to infer intent, automatically adjusting access rights based on the perceived goal rather than predefined rules. This approach could significantly enhance user experience while maintaining tight security controls.
As we navigate this complex landscape, it's crucial to remember that authorization is not just a technical challenge but a multifaceted business imperative. It requires a delicate balance between security, usability, and regulatory compliance. Regular security audits, penetration testing, and threat modeling should be integral parts of your authorization strategy.
In conclusion, as we hurtle towards a future dominated by AI, quantum computing, and hyper-connected ecosystems, robust and adaptive authorization systems will be the linchpin of digital trust. They will enable the seamless, secure interactions necessary for innovation to flourish in our interconnected world. The organizations that master this complex dance of access control will be best positioned to thrive in the digital frontier that lies ahead.
The Evolving Landscape of Cybersecurity: Beyond Authorization

While our deep dive into authorization has illuminated its pivotal role in the digital age, a recent incident involving CrowdStrike serves as a sobering reminder that the cybersecurity landscape is far more treacherous and multifaceted. Fast forward to July 2024, and we find the very sentinel we previously discussed not felled by an authorization breach, but by the double-edged sword of its own innovation.
In a twist of digital irony, CrowdStrike's attempt to fortify its defenses through a routine content configuration update for its Windows sensor unleashed a cascade of unintended consequences. The update, designed to enhance the Falcon platform's dynamic protection mechanisms, instead triggered a domino effect of system crashes across millions of Windows devices. This digital butterfly effect rippled through the arteries of our interconnected world, disrupting critical sectors from healthcare to finance, and from energy grids to transportation networks.
This incident throws into sharp relief the Gordian knot of modern cybersecurity, where even the guardians themselves can inadvertently become the architects of chaos. It underscores a crucial truth: in our hyper-connected digital ecosystem, the ramifications of even a well-intentioned tweak can reverberate far beyond the confines of authorization protocols, reminding us that in the realm of cybersecurity, vigilance must be as dynamic and multifaceted as the threats we face.
The 2024 crisis resulted from a faulty software update, in contrast to the 2023 incident's authorization failure. Specifically, a content configuration update for the Windows sensor, intended to enhance the dynamic protection mechanisms of CrowdStrike's Falcon platform, resulted in widespread Windows system crashes.
This incident highlights several crucial points:
- The Complexity of Modern Cybersecurity: Strong authorization systems are essential but only part of comprehensive cybersecurity. In our interconnected digital world, even well-planned changes can have unexpected and wide-ranging effects.
- The Double-Edged Sword of Automation: While automated updates and dynamic protection are crucial for addressing new threats, they can introduce risks that require careful management.
- The Importance of Thorough Testing: Revised version: With software updates impacting millions of systems at once, thorough testing and validation are now essential.
- The Need for Rapid Response and Transparency: CrowdStrike demonstrated effective incident response by quickly identifying, resolving, and openly communicating about the issue, reinforcing best practices in cybersecurity management.
Authorization systems are a critical component of our digital infrastructure. The CrowdStrike incidents of 2023 and 2024 serve as stark reminders that in the labyrinth of modern cybersecurity, even the Minotaurs can become ensnared. As we hurtle towards a future where quantum bits dance with neural networks and our digital selves become indistinguishable from our physical ones, we must recognize that our cyber defenses must evolve from mere walls to living, breathing ecosystems.
Imagine, if you will, an army of invisible sentinels, their watchful eyes scanning the digital horizon. These are not mere lines of code, but adaptive, learning entities, capable of anticipating threats before they materialize. They are the unsung heroes of our digital age, tirelessly weaving a protective cocoon around our data, our identities, our very way of life.
But these guardians cannot stand alone. They must be part of a symphony of security measures, each instrument playing its part in perfect harmony. From the staccato of secure development practices to the crescendo of incident response strategies, this cybersecurity orchestra must perform flawlessly, day in and day out, on a stage where the stakes are nothing less than the integrity of our digital civilization.
As we push the boundaries of what's possible in our interconnected world, let us not forget the silent watchers who make it all possible. They are the ones who ensure that when you make a mobile payment, your financial data doesn't become a hacker's jackpot. They are the ones who protect your autonomous vehicle from becoming a 2-ton missile controlled by malicious actors. They are the ones who safeguard the power grids, water systems, and communication networks that form the backbone of our society.
So the next time you effortlessly access your smart home system from halfway across the world, or when your AI assistant seamlessly coordinates your schedule across multiple platforms, take a moment to appreciate the invisible guardians working tirelessly behind the scenes. For in this brave new world of ours, they are the thin digital line between order and chaos, the silent sentinels standing watch over our digital dreams.
The challenge before us is clear: to forge cybersecurity strategies as dynamic, adaptive, and resilient as the threats they face. It's a never-ending game of digital chess, where the board is constantly shifting, new pieces are introduced without warning, and the stakes are nothing less than the future of our connected world.
Are we ready to play?

Don't forget to check out the weekly roundup: It's Worth A Fortune!







Member discussion